Abusing the Microsoft Word feature subDoc in phishing campaigns
Microsoft Office Exploitation
The Microsoft Office suite is known to have plenty of features that can be abused by attackers, red-teamers and security researchers, these features can be abused in such a way that gives the attacker unlimited possibilities and attack vectors, attacks can go from a simple NTLMv2 hash steal to Arbitrary Code Execution.
You might think that Microsoft Office is quite an uncommon way to execute malware, however it's not only used to execute malicious code. It's mainly used in red-team operations for phishing campaigns. The existence of Microsoft Office makes it for an ideal tool in phishing campaigns.
Abusing the Microsoft Word feature: subDoc
The subDoc field is an OOXML (Open Office XML) field implemented in Microsoft Word known to exist ever since from Microsoft Word 2007 to the Microsoft Word 2016. Its whole purpose is to embed a "subdocument" within a master document, for example, embedding an external Word document into a "master" document.
To add the subDoc field to your Word document is as easy as editing these files in the OOXML package (zip file):
word/_rels/document.xml.rels
word/document.xml
As we can see, to embed a subdocument to our master document, we need to provide the file path to the file, often when we can specify an external file path, we can access external SMB shares, that is, if we can depending on how mature the environment we're working on is. So then I tried to replace the Target field with an UNC path to an external SMB server. Upon opening the Word document I received a SMB request on my Responder client with the NTLMv2 Client (The victim's IP Address), the NTLMv2 Username (The victim's HOSTNAME\username) and the victim's NTLMv2 Hash, as shown on the screenshot below.
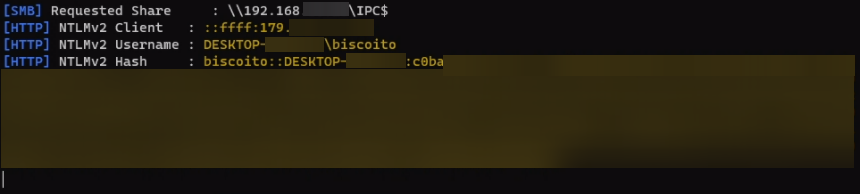
We managed to successfully steal the victim's NTLMv2 hash, however, there's one drawback from using this feature, which is that the hyperlink is visible on the Word page as shown in the screenshot below:
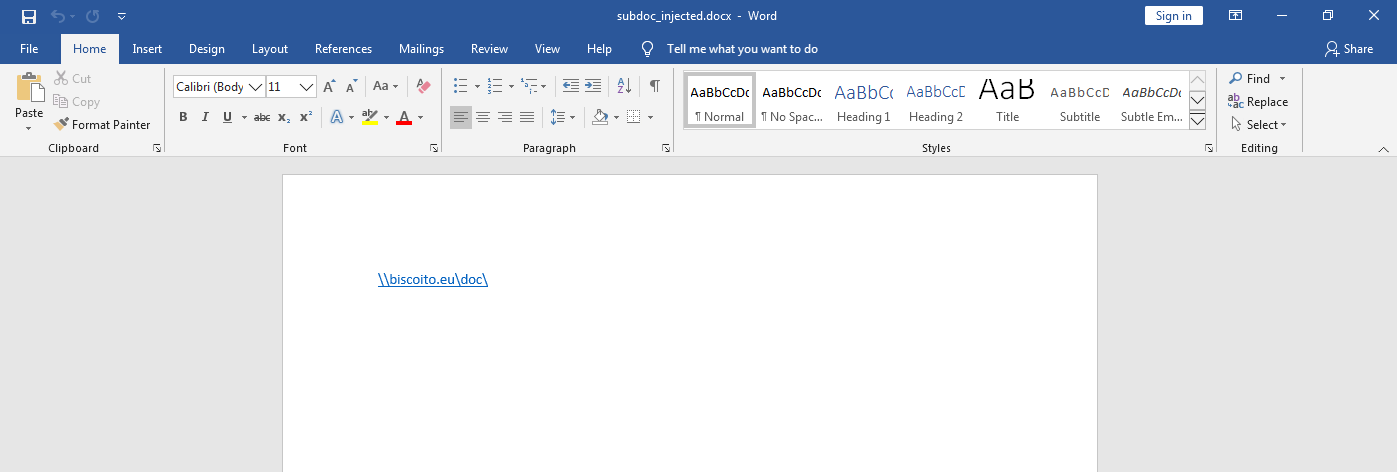
So then I started to mess around with the files inside the OOXML package and figured out that the styles.xml file contained all the styles for the Hyperlink, such as its color, font, theme, etc… as shown below:
word/styles.xml
By editing these fields I was able to change the Hyperlink color from the default one to white, so it would disappear on the page, and it did. Easy as that.
Now you have a completely stealthy and hidden NTLMv2 hash stealer.
Using go-subdoc to automate the whole process
Given how manual the whole process to craft a malicious Word document with subDoc is, I decided to write a PoC tool to automate the whole process in Go, it's called go-subdoc and you can find it on its GitHub repository: https://github.com/offsec-org/go-subdoc.
To use it is pretty simple, simply download one of the releases or install it to your GOPATH and provide the input file and target domain/ip address of the Responder or SMB share, as shown on the README for example:
It will generate a new malicious payload with the _injected name at the end.
Conclusion
Upon reviewing the Microsoft Word specifications, I found a field called subDoc that can be used to embed a document inside another, by providing it a file path, I managed to change that file path to an external SMB share and managed to steal the victim's NTLMv2 hash in a stealthy and hidden way.